Press Release: LinkDaddy Cloud Services - Innovative Cloud Solutions
Press Release: LinkDaddy Cloud Services - Innovative Cloud Solutions
Blog Article
Take Advantage Of Cloud Solutions for Boosted Data Safety And Security
In today's electronic landscape, the ever-evolving nature of cyber threats requires a positive approach towards guarding sensitive information. Leveraging cloud solutions offers an engaging option for companies looking for to strengthen their data protection measures. By delegating credible cloud company with data management, services can tap into a wealth of safety functions and advanced modern technologies that reinforce their defenses versus destructive actors. The inquiry develops: how can the usage of cloud services transform data safety and security techniques and supply a durable shield versus prospective susceptabilities?
Relevance of Cloud Safety
Ensuring durable cloud safety measures is paramount in guarding sensitive information in today's electronic landscape. As companies significantly rely upon cloud solutions to save and refine their data, the demand for strong safety and security protocols can not be overemphasized. A violation in cloud safety can have severe effects, varying from financial losses to reputational damages.
One of the primary factors why cloud protection is essential is the shared responsibility version employed by most cloud company. While the service provider is liable for securing the infrastructure, consumers are in charge of safeguarding their data within the cloud. This division of duties underscores the value of implementing robust safety measures at the individual degree.
In addition, with the proliferation of cyber risks targeting cloud settings, such as ransomware and data violations, organizations need to remain positive and vigilant in mitigating threats. This entails consistently updating security procedures, monitoring for dubious tasks, and enlightening workers on best practices for cloud security. By prioritizing cloud safety, companies can better safeguard their sensitive information and support the trust of their stakeholders and consumers.
Information Security in the Cloud

File encryption in the cloud normally involves the usage of cryptographic algorithms to clamber information into unreadable styles. Furthermore, numerous cloud service carriers supply file encryption devices to protect information at remainder and in transportation, improving general data security.
Secure Data Back-up Solutions
Data backup services play an important role in ensuring the strength and safety and security of information in case of unforeseen cases or information loss. Secure data backup remedies are essential parts of a durable data safety technique. By frequently backing up data to secure cloud web servers, organizations can alleviate the risks connected with data loss because of cyber-attacks, equipment failings, or human error.
Implementing protected data backup remedies includes selecting reputable cloud solution providers that use security, redundancy, and data honesty steps. Furthermore, information honesty checks ensure that the backed-up data stays tamper-proof and unchanged.
Organizations should establish automatic back-up timetables to ensure that information is consistently and effectively backed up without hand-operated intervention. When needed, regular screening of information reconstruction procedures is likewise essential to guarantee the effectiveness of the backup options in recovering data. By spending in safe and secure data backup options, companies can boost their data security pose and decrease the impact of prospective information violations or interruptions.
Function of Access Controls
Applying stringent gain access to controls is crucial for keeping the safety and stability of delicate details within organizational systems. Accessibility controls function as a crucial layer of defense versus unapproved access, making sure that just accredited people can view or adjust delicate data. By defining that can gain access to particular resources, organizations can restrict the threat of data breaches and unapproved disclosures.
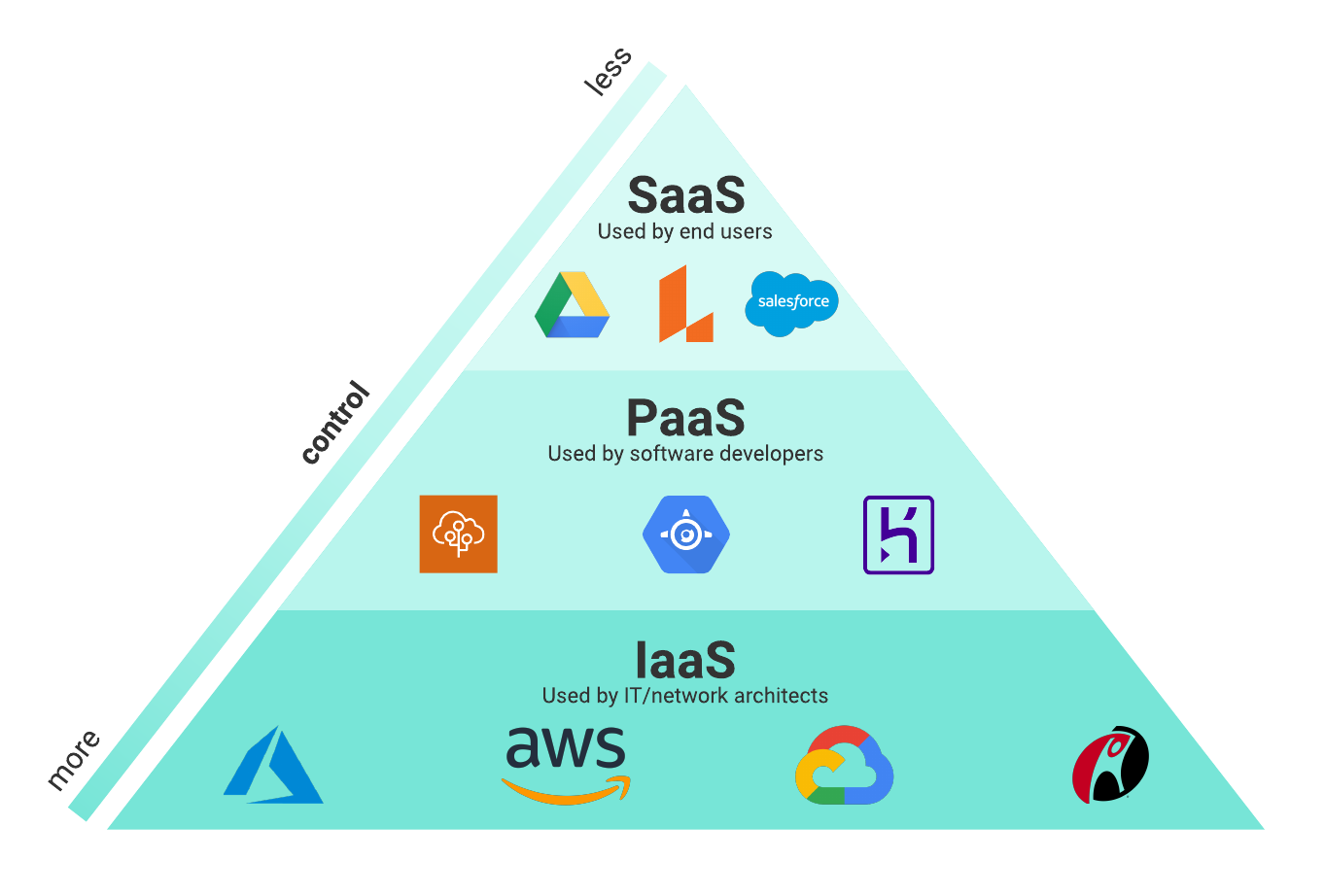
Routinely evaluating and updating accessibility controls is important to adjust to business modifications and evolving security risks. Continuous surveillance and auditing of gain access to logs can assist discover any suspicious activities and unapproved access efforts promptly. Overall, durable accessibility controls are fundamental in protecting sensitive info and mitigating security risks within business systems.
Compliance and Rules
Regularly guaranteeing conformity with appropriate guidelines and criteria is crucial for organizations to promote data safety and security and personal privacy actions. In the realm of cloud services, where data is frequently saved and refined on the surface, adherence to industry-specific laws such as GDPR, HIPAA, or PCI DSS is critical. These regulations mandate details information taking care of techniques to shield delicate information and guarantee individual personal privacy. Failing to follow these guidelines can result in serious charges, including penalties and lawsuits, harming a company's online reputation and count on.
Numerous suppliers use file encryption abilities, access controls, and audit routes to aid companies satisfy data protection criteria. By leveraging certified cloud solutions, companies can improve their data safety stance while fulfilling regulatory obligations.
Conclusion
To conclude, leveraging cloud solutions for improved data protection is necessary for companies to safeguard delicate details from unauthorized gain access to and possible breaches. By executing durable cloud protection procedures, including information security, safe and secure backup remedies, gain access to controls, and compliance with policies, companies can benefit from advanced safety and security steps and competence provided by cloud service companies. This helps mitigate threats successfully and guarantees the confidentiality, stability, and accessibility of data.

Information back-up options play an important function in guaranteeing the resilience and security of information in the occasion of unforeseen events or data loss. By routinely backing up data to safeguard cloud web see this site servers, organizations can reduce the dangers connected with data loss due to cyber-attacks, hardware failings, or human mistake.
Implementing secure data backup solutions involves choosing reliable cloud service companies that provide file encryption, redundancy, and data stability procedures. By spending in safe data backup solutions, businesses can site enhance their information safety pose and minimize the influence of potential information breaches or disturbances.
Report this page